H@cktivityCon 2021 CTF Writeups
Table of Contents
Had a lot of fun with this CTF and it’s always nice to see my amateur radio and infosec hobbies mixing together. Actually got around to doing a writeup this year too! I sometimes wonder if I should ever try joining a team for one of these, instead of always competing as a “solo” team. Maybe I’d do better than hovering around top 10% every time.

Warmups #
Six Four Over Two (50 points) #
We are provided with a short text file containing the string: EBTGYYLHPNQTINLEGRSTOMDCMZRTIMBXGY2DKMJYGVSGIOJRGE2GMOLDGBSWM7IK. Based on the name of the challenge, this could potentially be a Base32-encoded string. (Because \(\frac{64}{2} = 32)\) We test our theory using CyberChef and immediately get the flag: flag{a45d4e70bfc407645185dd9114f9c0ef}
Bass64 (50 points) #
We are provided with another text file, this time containing what appears to be a garbled mess of lines. However, simply disabling word wrap in Notepad allows us to see that it’s just ASCII word art for the string IGZsYWd7MzVhNWQxM2RhNmEyYWZhMGM2MmJmY2JkZDYzMDFhMGF9. Because it’s a relatively short string and I don’t know of anything that can convert from ASCII art back to text, we just manually parse and copy the text.
___ ____ _____ __ ____ __ _ _____ __ __ __ ___ _ _ __ _____ __ __ ____ ____ _ _ _ _____ __ ____ ________ __ __ ____ __ __ ____ __ __ _ __ ______ _ _ ____ _______ __ __ __ ____ _____ _ __ __ ____ _____ ___
|_ _/ ___|__ /__\ \ / /\ \ / /_| |___ | \/ |___\ \ / / |__ | \ | |\ \ / / _ \ __ _| \/ |___ \| _ \| |__ | \ | |_ __ ___ | ____| _ \ \ / /\ \ / /__ / |__ | \/ |/ ___| \/ |___ \| \/ |_ __ ___ | | _ __ __\ \ / /___ \ | | | __|__ /| _ \ \ / /__| \/ | _ \| ___| |__ | \/ |/ ___| ___/ _ \
| | | _ / // __\ V / \ \ /\ / / _` | / /| |\/| |_ /\ \ / /| '_ \| \| | \ \ /\ / / | | |\ \/ / |\/| | __) | |_) | '_ \| \| | '_ ` _ \| _|| | | | \ V / \ \ /\ / / / /| '_ \| |\/| | | _| |\/| | __) | |\/| | '_ ` _ \ _ | || '_ ` _ \ V / __) | | | |/ / / / | | | \ V /_ / |\/| | | | | |_ | '_ \ | |\/| | | _| |_ | (_) |
| | |_| |/ /_\__ \| | \ V V / (_| | / / | | | |/ / \ V / | | | | |\ | \ V V /| |_| | > <| | | |/ __/| _ <| | | | |\ | | | | | | |__| |_| | | | \ V V / / /_| | | | | | | |_| | | | |/ __/| | | | | | | | | |_| || | | | | | | / __/ |_| | < / /_ | |_| || | / /| | | | |_| | _| | | | || | | | |_| | _| \__, |
|___\____/____|___/|_| \_/\_/ \__,_|/_/ |_| |_/___| \_/ |_| |_|_| \_| \_/\_/ \__\_\/_/\_\_| |_|_____|_| \_\_| |_|_| \_|_| |_| |_|_____\__, | |_| \_/\_/ /____|_| |_|_| |_|\____|_| |_|_____|_| |_|_| |_| |_|\___/ |_| |_| |_|_| |_____\___/|_|\_\/____ |____/ |_|/___|_| |_|____/|_| |_| |_||_| |_|\____|_| /_/
|___/
Based on both the challenge name and the format of the string, we can assume that this is a Base64-encoded string. Putting this into CyberChef gives us the flag: flag{35a5d13da6a2afa0c62bfcbdd6301a0a}
Pimple (50 points) #
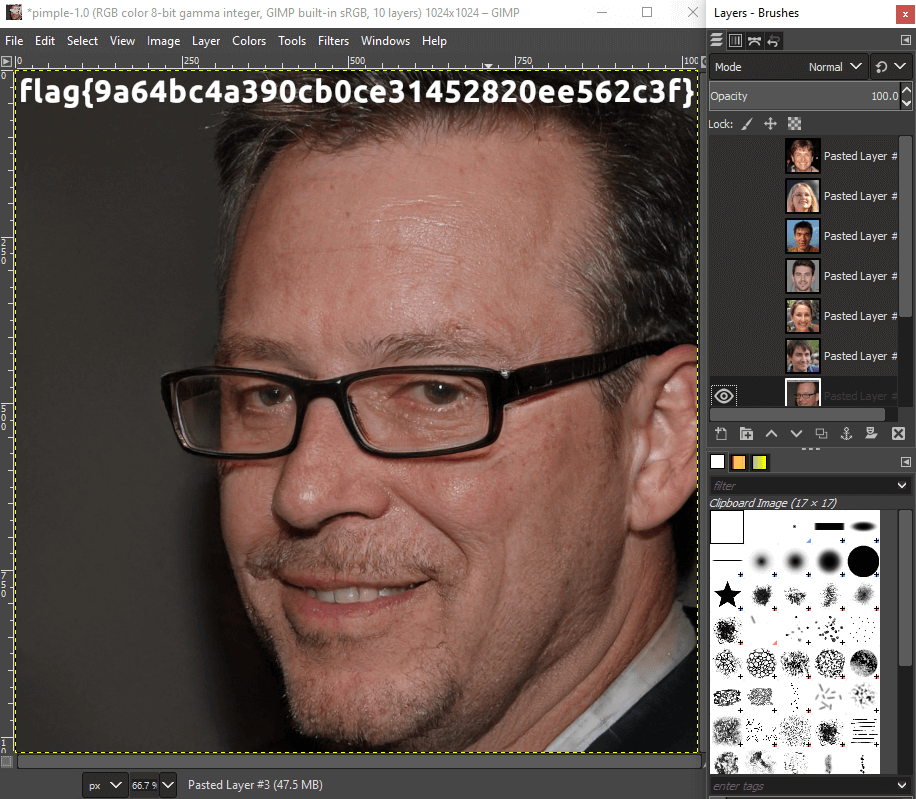
This one is pretty simple. Using file on attachment shows that it’s a GIMP file. Then after opening the file in GIMP and looking through the content, we find the flag printed on one of the inner layers: flag{9a64bc4a390cb0ce31452820ee562c3f}
$ file pimple
pimple: GIMP XCF image data, version 011, 1024 x 1024, RGB Color
Tsunami (50 points) #
Using file again, we discover that this is a .wav file.
$ file tsunami
tsunami: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, stereo 44100 Hz
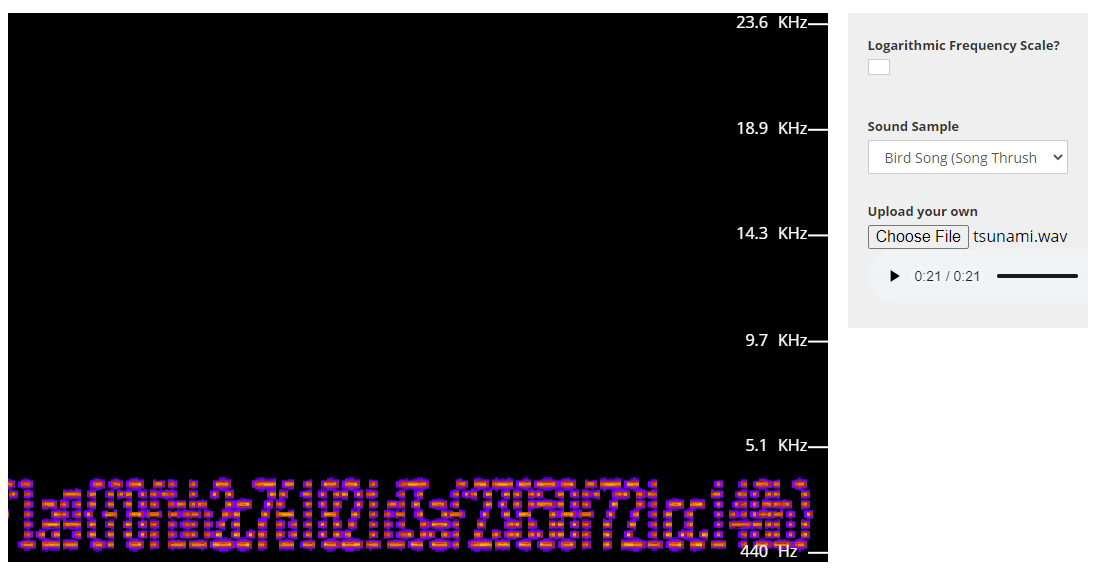
The end of the audio is a series of tones that makes me think it’s spectrogram steganography. After finding a website that let’s us view the spectrogram of an audio file(Academo), we see that those series of tones make up the flag value: flag{f8fbb2c761821d3af23859f721cc140b}. If it’s hard to make out the flag yourself, just remember that all of the letters are lowercase so they can’t be confused with a number.
Butter Overflow (50 points) #
This time we’re provided with three files.
- An executable file:
butter_overflow - The source code of the executable:
source.c - A
Makefilewe can use to compile the source code ourselves
After examining the source code, we discover the following information about the program’s behavior:
- Line 43 - Creates a buffer array that can store up to 512 bytes
- Line 51 - Directly saves user input into this buffer, without size checks
- Lines 48 & 10 - Runs the
give_flag()function if there’s a segmentation fault
So the solution is simple, if we provide enough input to the program to cause a buffer overflow, it’ll trigger a segmentation fault and give us the flag. Sure enough, sending 600 A’s to the challenge server prints out the flag: flag{72d8784a5da3a8f56d2106c12dbab989}
Oddball (103 points) #
Funnily enough, this warmup challenge ended up being worth more than some of the “real” challenges. Here, we are given an oddball file containing several lines of numbers.
0000000 067531 020165 067165 067543 062566 062562 020144 064164
0000020 020145 062563 071143 072145 066440 071545 060563 062547
0000040 035440 005051 072516 061155 071145 020163 067151 071040
0000060 067141 062547 030040 033455 020077 066510 066555 020041
0000100 067510 020167 062157 005041 063012 060554 075547 060462
0000120 031065 061462 033062 034143 060467 031546 034461 061062
0000140 031064 031543 063064 031544 033062 034063 061065 005175
0000160
After analyzing the file for a bit, we realize that there are no numbers greater than 7, so the file must be a list of octal numbers. As it turns out, the famous xxd tool has a lesser known uncle called od. But rather than hexdumps, this program creates octal dumps of files in the exact same format as the oddball file. Unfortunately, od doesn’t appear to have a reversal function like xxd does, so we have to make one ourselves. After taking out the first column of numbers, we can use the following python3 script to decode oddball.
from pwn import *
oct = """067531 020165 067165 067543 062566 062562 020144 064164 020145 062563 071143 072145
066440 071545 060563 062547 035440 005051 072516 061155 071145 020163 067151 071040 067141
062547 030040 033455 020077 066510 066555 020041 067510 020167 062157 005041 063012 060554
075547 060462 031065 061462 033062 034143 060467 031546 034461 061062 031064 031543 063064
031544 033062 034063 061065 005175""".split()
for num in oct:
# Decodes the octal string into its byte form
# ^──────────────┐
# Reverses the endianess of the byte so it prints correctly
# ^────┐ |
# Decodes the byte into a printable string
# ^────|─────────|───────┐
# V V V
print(p16(int(num, 8)).decode('utf-8'), end='')
Running this script provides us with the following output containing the flag:
You uncovered the secret message ;)
Numbers in range 0-7? Hmmm! How od!
flag{2a522c26c87af3192b42c34fd326385b}
Web #
Confidentiality (50 points) #
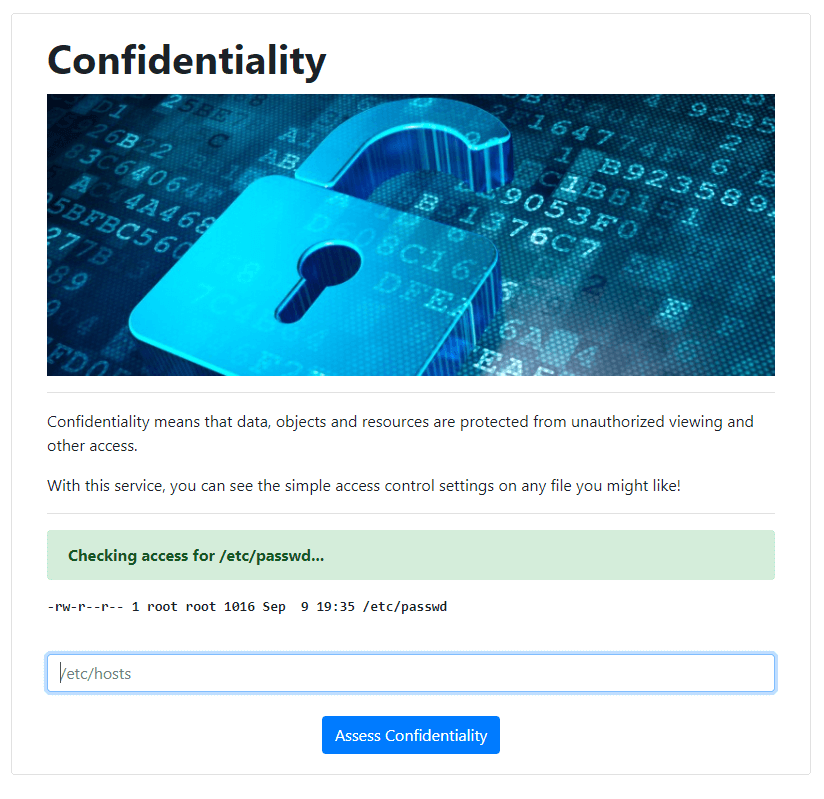
This challenge involves a simple command injection vulnerability. We’re provided with a web application that gives us the ability to check the access control settings for any given file on the server. To start, we test it out with a known file, /etc/passwd.
These results seem eerily similar to what ls -l does. It appears that the application is simply taking our input and appending it to an ls -l command. So if we wanted to see the files in our current directory, we could provide it with a period (.). Of course, we would normally just run ls -l on its own for the same effect, but the application rejects an empty input.
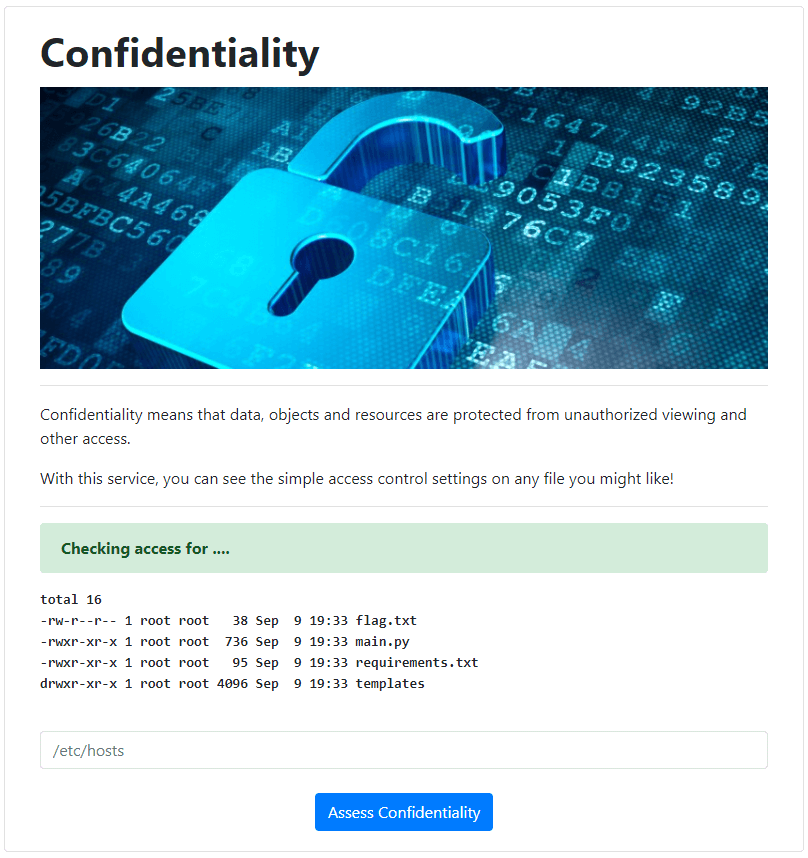
This is the exact output we would expect from an ls -l . command. So our goal now is to output the contents of the flag.txt file within this directory. To verify our command injection capabilities, we can use the ; character to append a second command to this line. By sending a request for ; whoami, we predict that the server will run the command ls -l ; whoami, showing us the current directory and username.
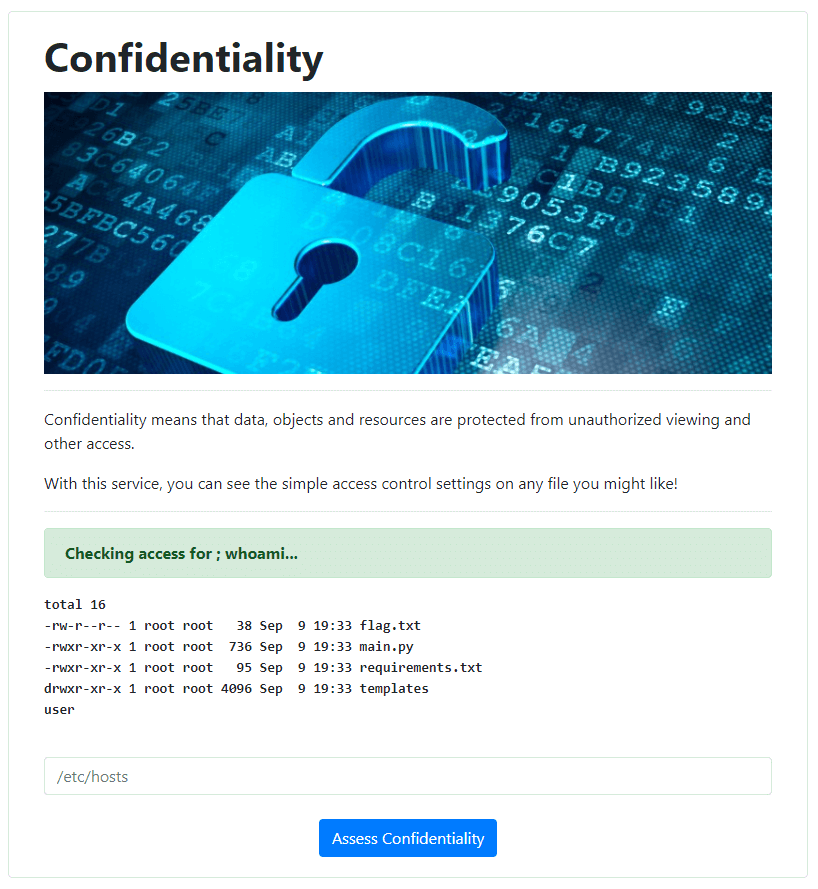
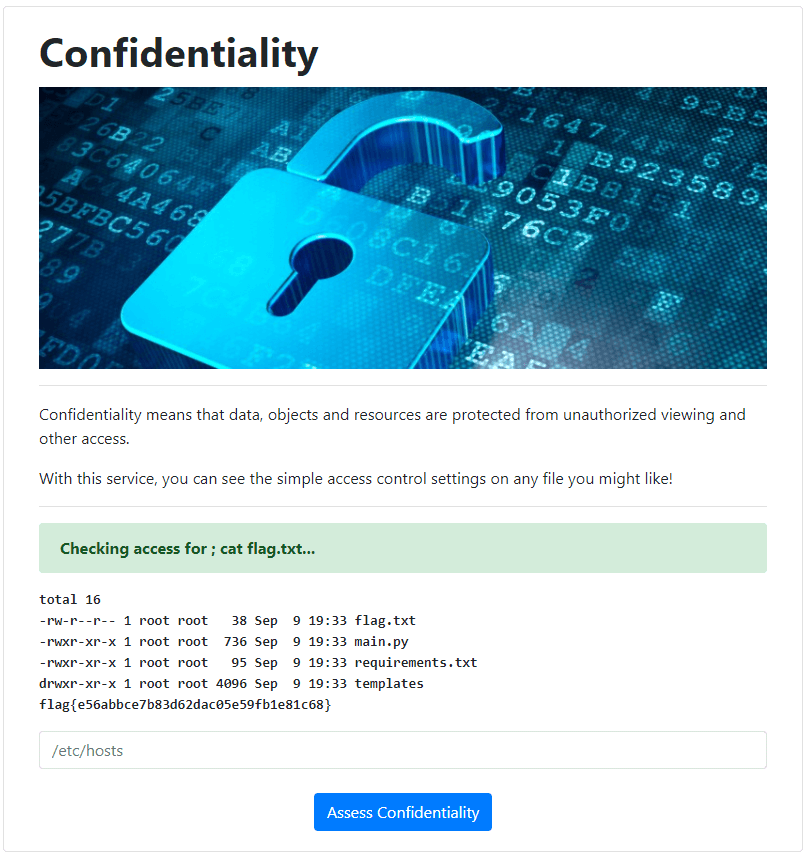
Success! This shows us that we have the ability to execute commands on the server. Now we just need to send a ; cat flag.txt request to output the flag, which ends up being: flag{e56abbce7b83d62dac05e59fb1e81c68}
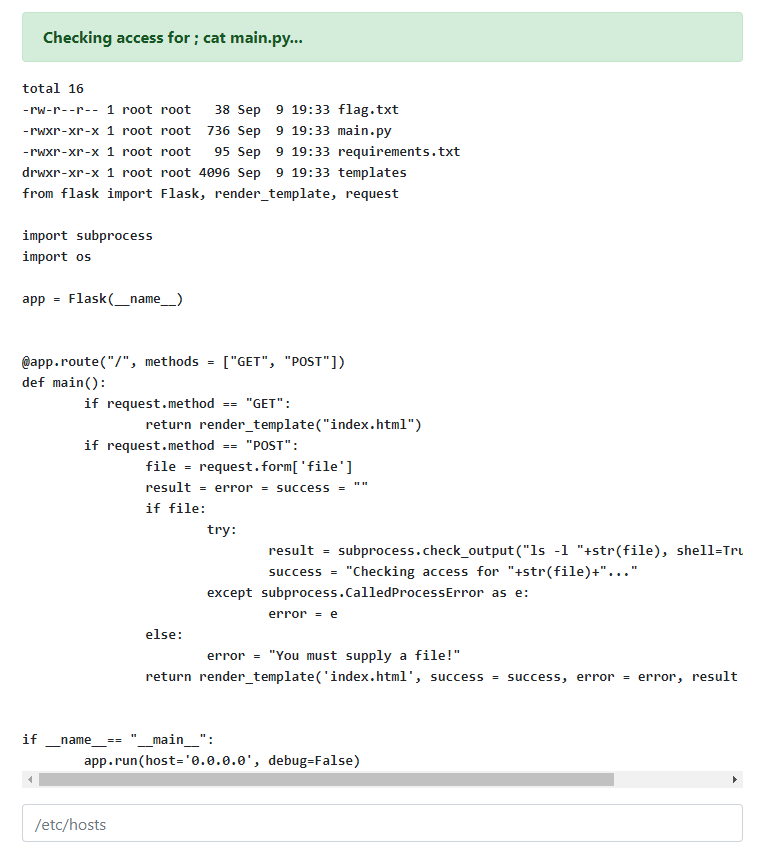
Bonus: If we wanted to, we can also see the source code for the application itself. A ; cat main.py request outputs the contents of main.py and shows how the application operates. And exactly how we predicted, the application is simply appending our input to the end of an ls -l command, without any verification or sanitization.
Titanic (50 points) #
This challenge involves leveraging a server-side request forgery (SSRF) to access sensitive, internal information. The website contains two main features that we will use: an admin login page and a URL capturer service.
The admin login is fairly normal. Since we obviously don’t have any admin credentials, we cannot make real use of this section right now. However, one thing of note about this page is the unique way it sends login attempts. Normally, logins would be sent as a POST request, with the username and password in the body. But here, the login attempt is made as a GET request, with the username and password in the URL. A username and password of test:test is performed with the URL http://challenge.ctf.games:31971/admin.php?uname=test&psw=test. While this behavior isn’t particularly useful to us right now, it will become very important later on.
Moving on to the URL capturer service. This service simply takes the URL we provide, makes a request to that URL on our behalf, and gives back a screenshot of the webpage. This service can allow us to perform an SSRF to disclose sensitive, local information on the server. It’s actually difficult to really call it an SSRF vulnerability because it’s clearly intended behavior. But to first validate that we can use it for SSRF, we will make a request to http://localhost and verify that we receive the same webpage.
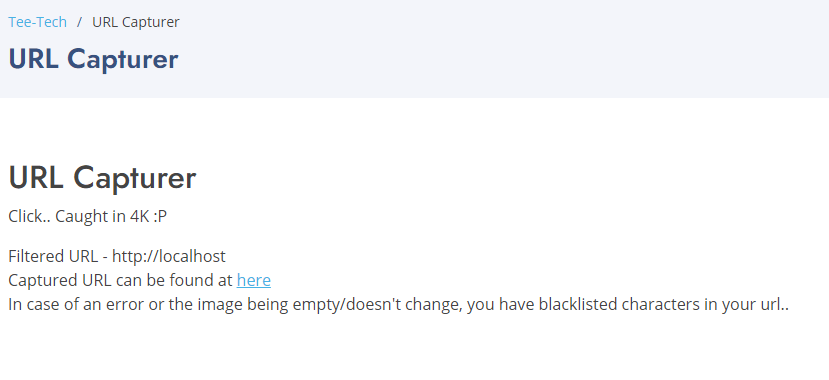
The request is successful! We receive back the loading circle for the website, showing that it is successfully making a request to http://localhost. As far as how to use it though, the robots.txt file for the website points to the /server-status page as an option. When we make a request to that page ourselves, it gives back a 403 Forbidden error. However, if we ask the server to request it locally at http://localhost/server-status, we get back the full status page for this webserver.
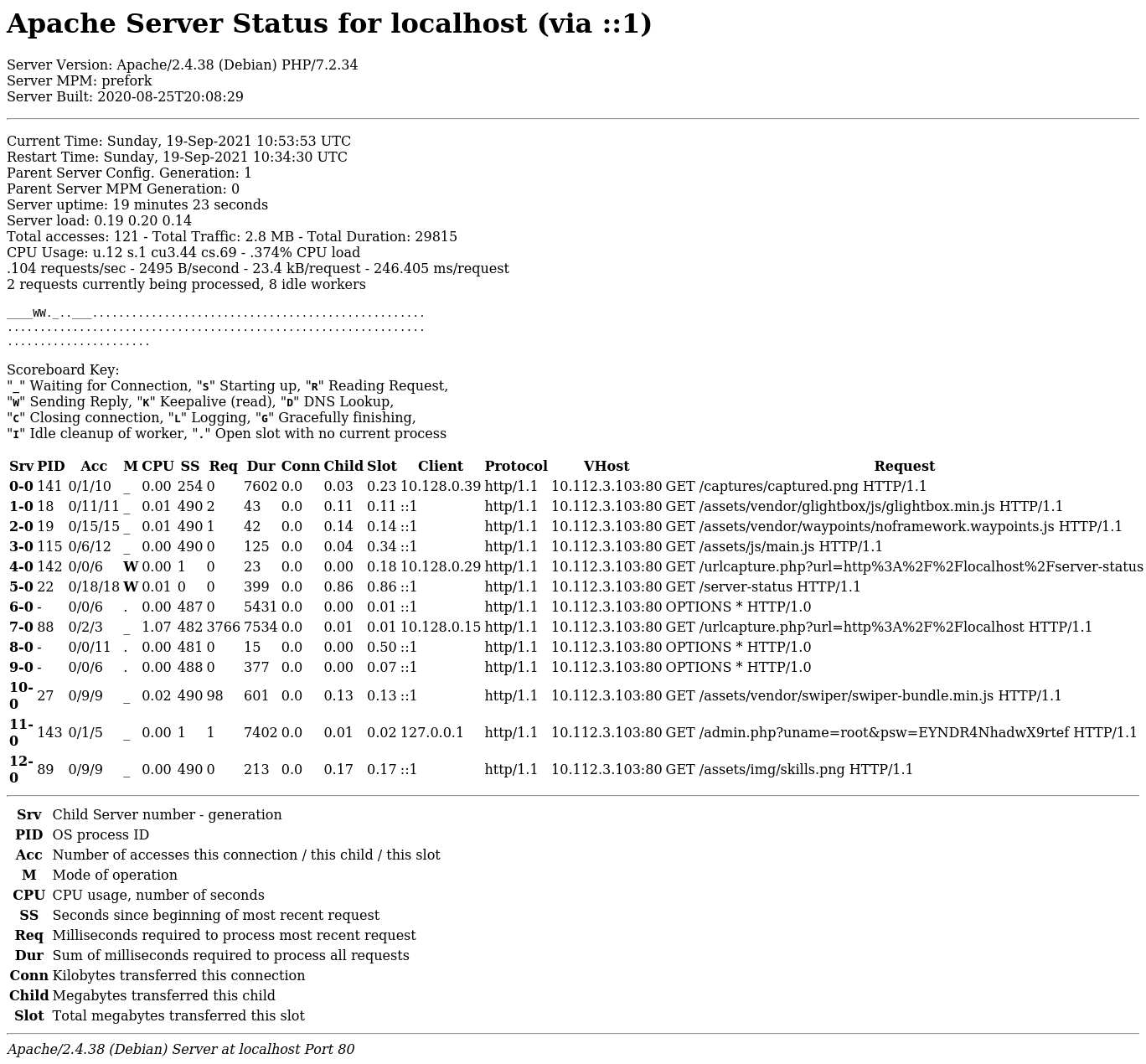
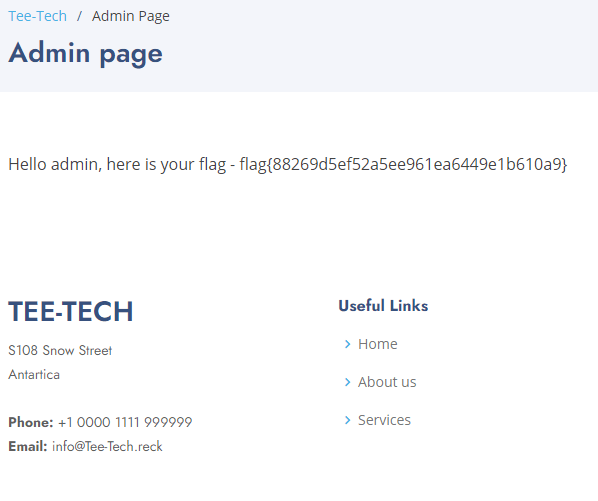
Remember how login attempts are made as a GET request? Because of that, now we can clearly see a username and password for a previously successful login attempt: root:EYNDR4NhadwX9rtef. Using these credentials, we can access the admin page and retrieve the flag: flag{88269d5ef52a5ee961ea6449e1b610a9}.
Cryptography #
N1TP (50 Points) #
This challenge is deceptively simple. When we first connect to the server, “Nina” provides us with the ciphertext of the flag. We should also note that the ciphertext changes between connections. After this, they give us the option to provide our own plaintext to see the resulting ciphertext. While providing the ciphertext, Nina also confirms that we’re dealing with a one-time pad (OTP).
Nina is correct in saying that OTPs are unbreakable. However, this is with the giant caveat that the OTP is used correctly. If you were to ever reuse a OTP’s key, like what Nina is doing here, it gives an attacker an opportunity to break the encryption. Even worse, if you reuse the key on plaintext that the attacker already knows, that OTP is completely broken.
The reason for this is that a OTP uses the exclusive OR (XOR) operation to perform its encryption and decryption. Normal use of an XOR \(\oplus\) cipher goes like this:
$$ \textbf{Encryption: } \text{Plaintext} \oplus \text{Key} = \text{Ciphertext} $$
$$ \textbf{Decryption: } \text{Ciphertext} \oplus \text{Key} = \text{Plaintext} $$
However, we if know the plaintext and ciphertext of a message, we can also compute the key using the properties of the XOR operation.
$$ \text{Plaintext} \oplus \text{Ciphertext} = \text{Key} $$
So using this principle, we can perform a known-plaintext attack on Nina’s OTP to derive the key. Our first step is to encrypt a plaintext value the same length of the flag. For this, we will choose 00000000000000000000000000000000000000.
After receiving back the ciphertext for this message, we can XOR the plaintext and ciphertext together to determine the OTP key using CyberChef. Finally, we can XOR the flag’s ciphertext and the key together to reveal the flag in plaintext: flag{9276cdb76a3dd6b1f523209cd9c0a11b}.
Miscellaneous #
Bad Words (50 points) #
This challenge generously gives us a bash shell on the server at the jump. The catch is that we’re placed into an extremely restrictive jailshell. If we attempt to use many of our common commands, such as ls, id, and whoami, the shell yells at us for using a “bad word”. Thankfully after testing several options, we finally have success with the command /bin/sh -i. This breaks us out of the jailshell and drops us into a non-restricted sh shell. A few ls commands reveals the path to the flag file in ~/just/out/of/reach/flag.txt, which we can cat to retrieve the flag: flag{2d43e30a358d3f30fe65cc47a9cbbe98}.
If you want to know how the jailshell works, its code is contained within the .bashrc file. It defines a bad_words() function that compares each argument in a user’s commands against a list of “bad words”. Then using the trap 'bad_words' DEBUG command, it forces this function to run before any command is executed by the user. If one of the arguments matches one of the bad words, it stops the user’s command from running. However, we are able to get past it because it only checks for bad words starting from the beginning of the argument. This is because of the regex they’re using for matching (^$i.*). The ^ character anchors the match to only from the beginning of the string. So although sh is a bad word, /bin/sh goes undetected because the preceding /bin/ breaks the match.
shopt -s extdebug
function bad_words() {
declare -a arr=("alert" "egrep" "fgrep" "grep" "l" "la" "ll" "ls" [...snip...] "less" "lessecho" "flag" "root")
for i in "${arr[@]}"
do
if [[ "$BASH_COMMAND" =~ ^$i.* ]]; then
echo "You said a bad word, \"$i\"!!"
return 1;
fi;
done
return;
}
trap 'bad_words' DEBUG
OSINT #
Jed Sheeran (50 points) #
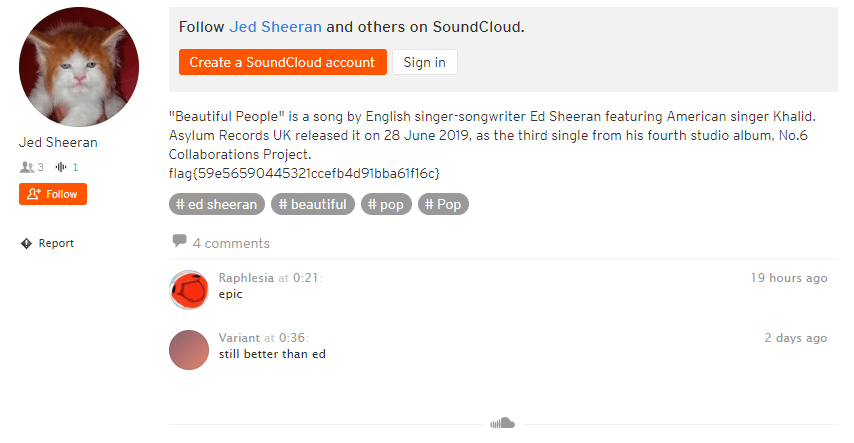
This challenge asks us to look for an aspiring music artist named Jed Sheeran. The actual discovery process is simple because a Google search for “Jed Sheeran” puts his SoundCloud as the first result. Jed’s profile has one song that contains a mess of beeps and squeaks.
This sound is actually a Slow-Scan Television (SSTV) signal, a method to transmit images as an analog signal. SSTV is popular within the amateur radio community particularly because it’s a way to send and receive images using very little bandwidth. It’s also common to see this in augmented reality games (ARG) or easter eggs as a way to hide pictures, like here in Portal 2. So to retrieve the flag from this audio file, all we need to do is decode the SSTV signal it’s playing.
One way to do it is to download an SSTV decoder app like Robot36 and hold your phone’s microphone up to your computer speakers. But you need to keep in mind that SSTV is an analog signal. So any noise in the signal will cause us to receive a degraded image. The more noise, the worse the image looks. However, we could use a something called a virtual audio cable, such as VB-CABLE, to connect our browser’s audio directly to an SSTV decoder program, like RX-SSTV. This will theoretically send the SSTV signal directly from SoundCloud to our decoder without any noise.
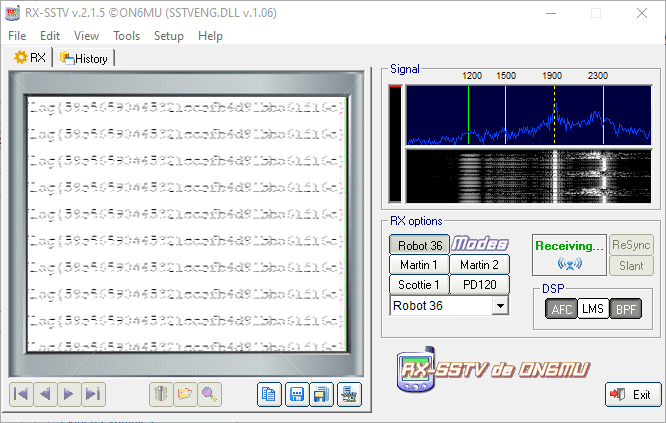
Well… the flag is clearly there, but it’s extremely hard to decipher. A lot of things could be happening here. SoundCloud could be compressing the SSTV audio before it’s stored, causing additional distortion in our image. It could also be that the flag’s text is too small for this SSTV mode. SSTV isn’t exactly known for sending extremely clear images, even in a perfect world. So people normally use bigger text in an image to compensate for that or switch to a more “robust” SSTV mode. The Jed Sheeran signal appears to be using the Robot 36 mode and is about 36 seconds long. Compare this to the following SSTV image I picked up from the International Space Station that uses PD120 and is about 120 seconds long. It has text about the same size as the Jed Sheeran signal, but this time it’s actually intelligible. Keep in mind that I received this signal from space, as well.

So where do we go from here? We could try really hard to determine what each character is. But, it seems that the challenge creator recognized how hard this was and decided to just put the flag in the song’s description: flag{59e56590445321ccefb4d91bba61f16c}.
Scripting #
Words Church (407 points) #
It appears that people either don’t like scripting or just don’t know how to script because these challenges ended up being worth a lot of points. The description tells us we’ll have to solve 30 word searches, so let’s connect to the server and see what we’re dealing with.
It looks fairly simple. We’re provided with a \( 15 \times 15 \) grid of characters and five words to find. The biggest challenge is really going to be how to parse everything. pwntools makes the sending and receiving part of the challenge easy, so all we have to worry about is how to process the information. The following python3 script let’s use receive the grid used for the game:
from pwn import *
io = remote('challenge.ctf.games', 32497)
io.recvuntil('>')
io.send('play')
# Header lines
io.recvlines(3)
# Grid lines
io.recvlines(16)
# Trailing lines
io.recvlines(2)
After putting this into the python3 interpreter, we verify that we’re correctly aligned to process the grid.
Python 3.9.2 (default, Feb 28 2021, 17:03:44)
[GCC 10.2.1 20210110] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> from pwn import *
>>> io = remote('challenge.ctf.games', 32497)
('>')
io.send('play')[x] Opening connection to challenge.ctf.games on port 32497
[x] Opening connection to challenge.ctf.games on port 32497: Trying 34.122.187.139
[+] Opening connection to challenge.ctf.games on port 32497: Done
>>> io.recvuntil('>')
b"Words Church v1.0\n\n
Let's play a game of wordsearch! We will display the grid\n
and offer you words to find. Please submit the locations of\n
each word in the format [(X,Y), (X,Y), (X,Y), ...] for each letter.\n\n
Please enter 'example' if you would like to see an \n
example, or 'play' if you would like to get started.\n
>"
>>> io.send('play')
>>>
>>> # Headers
>>> io.recvlines(3)
[b' Wordsearch # 1/30:',
b'\t 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 : X',
b'\t--- --- --- --- --- --- --- --- --- --- --- --- --- --- --- ---']
>>>
>>> # Grid lines
>>> io.recvlines(16)
[b' 0 | \t L P U C E U N K F C A Q T Q S H ',
b' 1 | \t Q L Q Q K E S P U V A W X T M E ',
b' 2 | \t E G O U H O U A Q D S K Z M T Y ',
b' 3 | \t L Z S I F O S U J S S E N A O V ',
b' 4 | \t I S M V D Y B B U G U O N J D J ',
b' 5 | \t S J Q E T N L A V K R K Z W S I ',
b' 6 | \t C P C R Y S E L K D E P S X A L ',
b' 7 | \t Q Q T E W F Z L I M D E U S C O ',
b' 8 | \t T G L D N N T Y J K I S Y L S B ',
b' 9 | \t N E Q J I I X H S K B L K O H S ',
b' 10 | \t V K M I U V U O K S K T Y E I T ',
b' 11 | \t I M N F G V S O Z O S H R T T E ',
b' 12 | \t H F Y K F S Q S Z J I I Z T J R ',
b' 13 | \t H U X E T R Y N R Z J M Z S U S ',
b' 14 | \t F R B D P Z K P K U N G A Q Y O ',
b' 15 | \t M S O T B F R P F R R P M M Z T ']
>>>
>>> # Trailing lines
>>> io.recvlines(2)
[b' ---',
b' Y ']
Translating the grid into a 2D-array is fairly trivial. All we have to do is split each line on whitespace to get a list of all characters, and then skip the first two characters that contain the Y coordinate and | separator. The following code does this for us:
# Process grid lines
for _ in range(16):
# Decode the input from a bytestring into a normal string
# ^─────────────────────────┐
# Split the string on whitespace, returning a list of each
# ^ character in the string
# └─────────────────────────│───────────────┐
# Skip the first two characters in the new list
# ^─────────────────────────│───────────────│──────┐
grid.append( io.recvline().decode('utf-8').split()[2:] )
# Test grid
print(grid)
# Output
"""
[['L', 'P', 'U', 'C', 'E', 'U', 'N', 'K', 'F', 'C', 'A', 'Q', 'T', 'Q', 'S', 'H'],
['Q', 'L', 'Q', 'Q', 'K', 'E', 'S', 'P', 'U', 'V', 'A', 'W', 'X', 'T', 'M', 'E'],
['E', 'G', 'O', 'U', 'H', 'O', 'U', 'A', 'Q', 'D', 'S', 'K', 'Z', 'M', 'T', 'Y'],
['L', 'Z', 'S', 'I', 'F', 'O', 'S', 'U', 'J', 'S', 'S', 'E', 'N', 'A', 'O', 'V'],
['I', 'S', 'M', 'V', 'D', 'Y', 'B', 'B', 'U', 'G', 'U', 'O', 'N', 'J', 'D', 'J'],
['S', 'J', 'Q', 'E', 'T', 'N', 'L', 'A', 'V', 'K', 'R', 'K', 'Z', 'W', 'S', 'I'],
['C', 'P', 'C', 'R', 'Y', 'S', 'E', 'L', 'K', 'D', 'E', 'P', 'S', 'X', 'A', 'L'],
['Q', 'Q', 'T', 'E', 'W', 'F', 'Z', 'L', 'I', 'M', 'D', 'E', 'U', 'S', 'C', 'O'],
['T', 'G', 'L', 'D', 'N', 'N', 'T', 'Y', 'J', 'K', 'I', 'S', 'Y', 'L', 'S', 'B'],
['N', 'E', 'Q', 'J', 'I', 'I', 'X', 'H', 'S', 'K', 'B', 'L', 'K', 'O', 'H', 'S'],
['V', 'K', 'M', 'I', 'U', 'V', 'U', 'O', 'K', 'S', 'K', 'T', 'Y', 'E', 'I', 'T'],
['I', 'M', 'N', 'F', 'G', 'V', 'S', 'O', 'Z', 'O', 'S', 'H', 'R', 'T', 'T', 'E'],
['H', 'F', 'Y', 'K', 'F', 'S', 'Q', 'S', 'Z', 'J', 'I', 'I', 'Z', 'T', 'J', 'R'],
['H', 'U', 'X', 'E', 'T', 'R', 'Y', 'N', 'R', 'Z', 'J', 'M', 'Z', 'S', 'U', 'S'],
['F', 'R', 'B', 'D', 'P', 'Z', 'K', 'P', 'K', 'U', 'N', 'G', 'A', 'Q', 'Y', 'O'],
['M', 'S', 'O', 'T', 'B', 'F', 'R', 'P', 'F', 'R', 'R', 'P', 'M', 'M', 'Z', 'T']]
"""
The next step is to determine how to receive the words we need to search for. After we receive the grid lines, the questions are sent to us in the following format: LIEU: >. All we need to do here is extract the word, which is very easy to do using split() again.
# Receive input until we hit the '>' character
question = io.recvuntil('>').decode('utf-8')
# Split the line on the ':' character and take everything before the ':'
word = question.split(':')[0].strip()
Now that we have our grid and words in a format we can process, it’s time to create the searching functions. While I’m sure there are super fast algorithms specifically designed to solve this problem, we’re going to stick with the naïve solution: go through every coordinate that matches the first letter of the word and search out from all eight directions to see if the rest of it matches. Here we have two components to design, the function to search through the entire grid, and the function to search out from a position to determine if the word matches. I’ve implemented them both in python3, as seen below:
# Search from a given (x,y) position out a given direction
# and return the positions of matching characters.
# Returns an empty list `[]` if the match fails.
def direction_search(word, grid, x, y, x_delta, y_delta):
tiles = []
for c in word:
# If this tile doesn't match the current character,
# return an empty list.
# The position also wraps around the edges of the grid.
if grid[y % len(grid)][x % len(grid)] != c:
return []
else:
# If we're still matching, add this position as an
# (x, y) tuple to the position list.
tiles.append( (x, y) )
# Move in the given direction
y += y_delta
x += x_delta
return tiles
# Search each tile in the grid and determine if the word is found
# in any 8 directions from each tile.
# Returns list of positions if the word is found, empty list `[]`,
# if not.
def word_search(word, grid):
for (y, row) in enumerate(grid):
for (x, tile) in enumerate(row):
# If this tile matches the first letter of the word, then
# check if the rest of the word is found in any of the
# 8 directions from this position.
if tile == word[0]:
for x_delta in [-1, 0, 1]:
for y_delta in [-1, 0, 1]:
search = direction_search(word, x, y, grid, x_delta, y_delta)
if len(search) > 0:
return search
return []
Finally, we can combine all of these elements in the final script and run it to solve the challenge to receive the flag: flag{ac670e1f34da9eb748b3f241eb03f51b}.
#!/usr/bin/python3
from pwn import *
import sys
def direction_search(word, grid, x, y, x_delta, y_delta):
tiles = []
for c in word:
if grid[y % len(grid)][x % len(grid)] != c:
return []
else:
tiles.append( (x, y) )
y += y_delta
x += x_delta
return tiles
def word_search(word, grid):
for (y, row) in enumerate(grid):
for (x, tile) in enumerate(row):
if tile == word[0]:
for x_delta in [-1, 0, 1]:
for y_delta in [-1, 0, 1]:
search = direction_search(word, grid, x, y, x_delta, y_delta)
if len(search) > 0:
return search
return []
def main():
# Connect to the challenge server
port = int(sys.argv[1])
io = remote('challenge.ctf.games', port)
# Start a game
io.recvuntil('>')
io.send('play')
for _ in range(30):
# Skip header lines
print(io.recvline().decode('utf-8').strip())
io.recvlines(2)
# Process grid
grid = []
for _ in range(16):
grid.append( io.recvline().decode('utf-8').split()[2:] )
# Skip trailing lines
io.recvlines(2)
# Answer questions
for _ in range(5):
question = io.recvuntil('>').decode('utf-8')
word = question.split(':')[0].strip()
answer = word_search(word, grid)
io.sendline( str(answer).encode('utf-8') )
# Skip post-game lines
io.recvlines(3)
# Print the final output
print(io.recvrepeat(5).decode('utf-8'))
if __name__ == "__main__":
main()
OTP Smasher (283 points) #
This is a pretty interesting challenge because it requires us to do some optical character recognition (OCR). We’re presented with a simple webpage displaying a picture of numbers, an submission field, and a counter in the upper-left. Chrome DevTools also shows that the page also attempts to display the image flag.png. Based on the challenge’s name, the number picture might be intended to act as a one-time password (OTP). Submitting the OTP increments the upper-left counter by one and waiting too long to submit another OTP resets it to zero.

While this challenge was up, the creator eventually decided to increase the length of time allowed until a reset to help make the challenge a bit easier. So right now, we could technically manually submit 45 passwords to get the flag. But of course, that is no fun learning-wise and no fun because it’s super tedious. Using Chrome DevTools, we were able to figure out the format of the submission: a POST request to the main page with the password in a field called otp_entry. Using this information, we are now able to automate OTP submissions.
import requests
from bs4 import BeautifulSoup as bs
# Send the current `otp` to the server
post = requests.post(f"http://challenge.ctf.games:{port}/", data={"otp_entry":otp})
# Print out the current counter value
print( bs(post.text, 'html.parser').p )
The remaining problem is how to know what numbers to send? To accomplish this, we will make use of a software called Tesseract and its companion Python module, pytesseract. Combining this with the requests module to download the image and the PIL module to store the image, we can now automate OCR on the images to determine the OTP’s numbers.
import requests
import pytesseract
from PIL import Image
from io import BytesIO
# Retrieve the current OTP image
get = requests.get(f"http://challenge.ctf.games:{port}/otp.png")
# Save the image into a PIL Image object
image = Image.open(BytesIO(get.content))
# OCR the image to determine the OTP
otp = pytesseract.image_to_string(image).strip()
This gives us an 80% solution to the challenge. I say 80% because while it works most of the time, it fails enough that we have to manually step in every once in awhile. There’s probably a way to train tesseract to better recognize the OTP numbers, but we won’t dive into that realm for this challenge. For now, we’ll just check if the string from tesseract is a number. If it isn’t, then have the user type in the OTP manually.
# See if we get an error when converting the OTP to a number
try:
int(otp)
except:
# If the OTP isn't a number, make the user type it in manually
otp = input(">")
Now that all of our components are created, we can combine them into the final script that’ll automatically send the OTPs to the server until it sees the flag: flag{f994cd9c756675b743b10c44b32e36b6}.
import requests
import pytesseract
import sys
from PIL import Image
from io import BytesIO
from bs4 import BeautifulSoup as bs
port = int(sys.argv[1])
while True:
# Retrieve the current OTP image
get = requests.get(f"http://challenge.ctf.games:{port}/otp.png")
# Save the image into a PIL Image object
image = Image.open(BytesIO(get.content))
# OCR the image to determine the OTP
otp = pytesseract.image_to_string(image).strip()
print(f"OTP - {otp}")
# See if we get an error when converting the OTP to a number
try:
int(otp)
except:
# If the OTP isn't a number, make the user type it in manually
otp = input(">")
# Send the current `otp` to the server
post = requests.post(f"http://challenge.ctf.games:{port}/", data={"otp_entry":otp})
# Print out the current counter value
print( bs(post.text, 'html.parser').p )
# Check if the flag image is available yet
flag = requests.get(f"http://challenge.ctf.games:{port}/flag.png")
if flag.status_code != 404:
# If we find the flag, save it and end the script
print("Flag found")
with open("flag.png", "wb") as f:
f.write(flag.content)
exit()
